The Costs of SQLCipher for Android
Being able to get high-grade encryption for one dependency and (seemingly) one line of code in the app seems wonderful. And, in truth, in scenarios that need encryption, it is wonderful. It is even both “free as in beer” and “free as in speech”.
However, there are costs… just not in terms of money or rights.
APK Size
The debug build of ToDoCrypt is 10MB. Of that, nearly 6MB comes from NDK binaries:
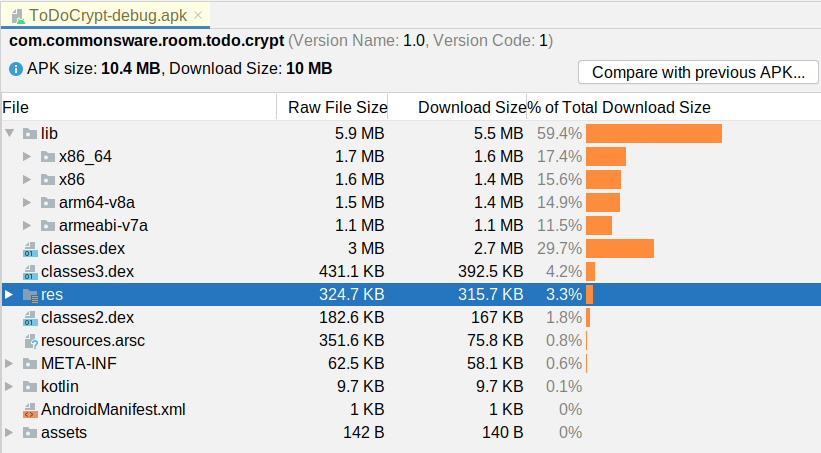
ToDoCrypt Debug Build
SQLCipher for Android includes a full copy of SQLite (with the SQLCipher extensions installed), for four CPU architectures. Using ABI splits or App Bundles, the cost for individual users can be a lot less, dropping that 6MB to 1-2MB. For some apps, this will not be a big problem; for other apps (and other user bases), adding that kind of size to the APK could be a deal-breaker.
Runtime Performance
Considering that everything is being encrypted and decrypted, the performance of SQLCipher for Android is fairly reasonable.
The biggest expense is when you open the database. That usually is when those NDK libraries will be loaded. Also, SQLCipher uses “key stretching” (thousands of rounds of PBKDF2) to convert your supplied passphrase into the actual encryption key, and this takes a bit of time. So, if your app loads data out of the database when the app starts, as ToDoCrypt does, this make take longer than you are used to. This specific edition of ToDoCrypt does not have a loading state, and depending on your test device, you will see why you need one — the UI briefly shows an empty state before any to-do items get loaded. However, since Room and modern Android architecture tend to steer developers towards opening the database just once per process, this cost is only incurred once per process.
After that, individual database operations are more expensive, but usually not dramatically more expensive. The cost of the encryption and decryption will be roughly proportional to the amount of data that needs to be encrypted or decrypted. As a result:
- Small database operations will not be perceptively slower with SQLCipher for Android than with plain SQLite
- Large database operations — ones that were somewhat painful already — may be a substantially more painful
This just means that you will need to spend some extra time in optimizing your database access, such as adding indices to avoid SQLCipher for Android having to decrypt an entire table to walk through all rows in a “table scan”-style query.
Complexity
The code changes in the chapter were trivial. That is because our approach towards managing the passphrase was trivial. Unfortunately, that also means that the security benefit is trivial, as an attacker would not have a difficult time finding that hard-coded passphrase.
In the end, the complexity of SQLCipher for Android comes not from the library, but rather from passphrase management. We will explore that more in the next chapter.
Prev Table of Contents Next
This book is licensed under the Creative Commons Attribution-ShareAlike 4.0 International license.